One of the biggest advantages that wireless connection brings to its users is the possibility of accessing the internet anywhere (malls, cafes, shops, markets etc.) without needing cables. The result is easier access to information and increased mobility for everyone.
Our users are talking about the best resources for checking your Wi-Fi status and who is using it . Join the conversation now!
After the dawn of the wireless connection, however, it didn’t take long before most devices started supporting Wi-Fi. This has ended up creating amongst users the need to have a wireless router at home.
The problem is this: just as you can connect to wireless networks in a mall, for example, it could be that your neighbors are also connecting to your network, “stealing” your bandwidth or accessing your folders and files.
Ever wondered what WiFi actually looks like? Click Here to Find Out

Ever wondered what WiFi actually looks like?
How do you find out if someone is using your internet without your permission? Below you will find some tips and solutions to avoid letting any Wi-Fi “hackers” interfere with your internet browsing and compromise your security.
How Do I Know if Someone Is Stealing my Wi-Fi Connection?
Router lights

Although this is not an accurate or even recommended method, it could be useful for a first diagnosis, quickly indicating if someone is stealing your internet. It basically consists of analyzing the router’s lights.
Usually these devices have lights that indicate the traffic through the network. These lights blink according to the amount of data the router is transferring. To use this method you must turn off every single wireless device in the house and check if the traffic light continues to flash.
If the LED indicator blinks frantically even with all devices with wireless connection turned off, there is a good chance that someone is using your internet. However, before taking any drastic measures use one of the following methods presented in this article just to be sure.
List of Apparatuses
The router settings center can be very useful to check if you have any unauthorized devices connected to your network. The IP address for center settings’ access is different for each type of router. One way to find out the IP access is by using the command prompt.
Press the shortcut “Win + R” and in the screen that appears, type “cmd”. Now, at the command line, type “ipconfig” and look for the “Default Gateway” line. Usually the IP listed on this line is the one that gives access to the router’s settings.
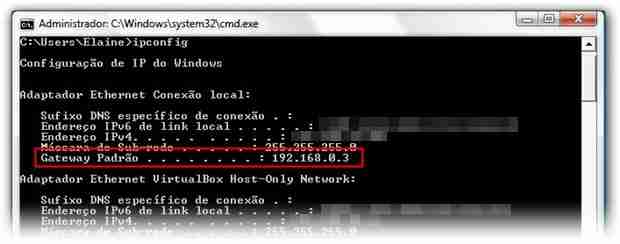
Once you have the IP address enter in the address bar, of your browser, the username and password to access the router and wait for the configuration screen to load.
Once again, all routers are different so in each manufacturer and model the list of connected devices is found in a different place. However, companies follow a naming pattern. Therefore, to find the list of recognized devices on the network, look for options such as “Device List”, “Attached Devices” or “My Network”.
List of devices present connected to the router
Lists typically provide the connected devices’ MAC address and IP address. Compare the devices with the electronics you have at home that allow you to access the internet. At the end of the comparison, if there is any item left on the list, it may be compatible with your neighbor’s wireless card.
How to enable private browsing mode on different browsers Read now
How to enable private browsing mode on different browsers
Monitoring through software
If you do not want to access the router settings to find out if someone is improperly using your internet, you can use applications developed exclusively for network monitoring.
For management, monitoring and security of wireless networks, two good program options are Zamzom Wireless Network Tool Basic Version and WiFi Manager, both are free and easy to use.
Network monitoring, in general, can be done using programs such as BitMeter , Wireshark , NetWorx and many others. With them, you can track data traffic on the network and verify if information flow is not greater than it should be. Some of them, even, allow you to see which devices are consuming more bandwidth.
What to do if somebody is stealing your internet?
And if you come to the conclusion that they are actually using your internet without the proper permission, what do you do? The first attitude is to protect your network by entering passwords and access filters.
Calm down and solve everything peacefully!
One of the best methods of protection is to filter access through the boards’ MAC address. Since the devices’ physical address works as if it were a fingerprint, which means it is unique, limiting access to the network through it is a great option.
Another alternative is to change the passwords for WPA2-AES, which is safer than the others. Changing the password itself can also be a solution. Remember that a good password is composed of numbers, letters and special characters and have no connection with the user’s personal life.
This article was originally published on April 26th 2017.